MalumPOS Malware Targets PoS Systems Running On Oracle Micros
Yet another point of sale malware attack! Researchers at security firm Tend Micro have discovered a new attack tool dubbed "MalumPOS" that is designed to collect data (card holder's name, account number and etc.) from PoS systems running on Oracle Micros.
Micros, a popular platform used in the hospitality, food and beverage,
and retail industries. According to Oracle, the micros is used at over
330,000 customer sites in 180 countries.
"MalumPOS uses various techniques inorder to prevent itself from being
detected. To some degree, these techniques are not particularly
sophisticated and are an attempt to hide in plain sight"
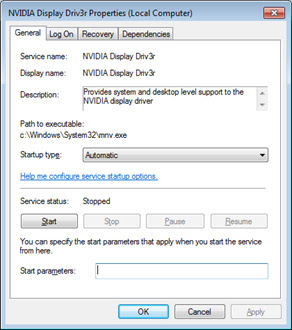
Once installed in a system, the MalumPOS malware disguises itself as the "NVIDIA Display Driver":
The interesting thing about MalumPOS malware is its versatility, the capability to reconfigure for any PoS system.
Every time the magnetic stripe of a credit card is swiped, the malware can steal customer credit card data from an infected systems' RAM.
You might also like: How Anonymous Hackers Changed the World (Documentary Film)
It also targets Oracle Forms, Shift4 systems, and the Web-based PoS systems accessed through Internet Explorer.
The research also shows that the MalumPOS Malware has some similarities with an older PoS threat called Rdasrv.
Get more technical information about MalumPOS malware[pdf] here.
Every time the magnetic stripe of a credit card is swiped, the malware can steal customer credit card data from an infected systems' RAM.
You might also like: How Anonymous Hackers Changed the World (Documentary Film)
It also targets Oracle Forms, Shift4 systems, and the Web-based PoS systems accessed through Internet Explorer.
The research also shows that the MalumPOS Malware has some similarities with an older PoS threat called Rdasrv.
Get more technical information about MalumPOS malware[pdf] here.